- •Quantum cryptography could eventually break today’s crypto security, including ECDSA and RSA.
- •CRQCs may expose private keys and digital signatures, posing systemic risks for blockchains.
- •HNDL attacks mean adversaries may already be storing blockchain data to decrypt in the future.
- •PQC offers protection with new NIST-approved algorithms like Kyber, Dilithium, and Falcon.
- •Users should minimize public key exposure, use cold storage for long-term holds, and keep wallets updated.
Cryptocurrency and blockchain technology rely on cryptography to secure assets and transactions. But a new kind of computing power; quantum computing, is emerging as a potential threat to those cryptographic shields. You might have heard whispers that quantum machines could one day “break Bitcoin” or crack into your digital wallet. The question is, how real is this threat, and what does it mean for everyday crypto holders and traders?
This explainer will examine the concerns surrounding quantum cryptography, clarify terms such as CRQC and HNDL, and assess the measures that individuals and the broader industry can adopt to safeguard digital assets in a post-quantum environment.
Quantum computing uses special processors called qubits that can calculate many possibilities at once.
For crypto users, that means these machines could eventually solve the math that protects private keys
and digital signatures, so wallets and blockchains must upgrade over time.
Why Do Quantum Computers Threaten Cryptography?
The power of quantum computing sounds exciting, until you realize how it interacts with cryptography (the math that secures our digital information). Modern cryptographic systems (like the encryption and digital signatures that protect your bank transactions, emails, and yes, cryptocurrencies) rely on certain math problems being really hard for classical computers to solve. For example:
- The security of RSA encryption relies on the fact that factoring a huge number (breaking it down into prime factors) is astronomically difficult for classical computers.
- The security of Bitcoin and Ethereum wallets relies on the difficulty of the elliptic curve discrete logarithm problem (ECDSA), essentially meaning it’s infeasible to derive a private key from a public key.
A sufficiently powerful quantum computer, known as a Cryptographically Relevant Quantum Computer (CRQC), could break the math that secures today’s encryption and digital signatures. Using algorithms like Shor’s algorithm, such a machine could unravel problems once thought impossible, threatening the security of trillions in digital assets.
How soon could this happen? No one knows for certain. A 2024 U.S. government report estimated a 17–34% chance of a CRQC by 2034 capable of cracking RSA-2048 in a day, while others push the timeline into the 2040s. Some believe progress may stall, while others warn it could accelerate, with “Q-Day” arriving as early as 2028. What experts agree on is that the threat is not if but when, and since transitioning to new algorithms takes years, preparation must start now.
CRQC (Cryptographically Relevant Quantum Computer):
A quantum computer with enough power to break current cryptographic systems. It could extract private keys from public keys or invalidate today’s digital signatures. None exist yet, but development is expected.
HNDL (Harvest Now, Decrypt Later):
A tactic where adversaries store encrypted data or public keys today, planning to decrypt them once quantum machines are strong enough. For crypto, it means public keys and transaction data can already be collected for future exploitation.
PQC (Post-Quantum Cryptography):
New cryptographic algorithms designed to withstand quantum attacks. They run on classical computers and are based on mathematical problems believed to remain secure even against quantum capabilities.
How Could Quantum Threaten Cryptocurrency?
Cryptocurrencies like Bitcoin and Ethereum are secured by cryptographic algorithms. If those algorithms get broken by a quantum computer, there are two major areas of risk:
Wallet Security (Private Keys and Public Keys)
You prove ownership of your crypto (and authorize transactions) by using a private key to create a digital signature. The world sees your public key (or an address derived from it) and the signature, and they trust it because, with today’s math, no one can figure out your private key from your public key or forge your signature. Quantum changes that. A quantum attacker with a CRQC could deduce your private key from your public key in short order, or fake your signature, thus stealing your funds or impersonating you on the blockchain.
For Bitcoin, this threat is especially acute for addresses that have already revealed their public keys. A powerful quantum computer could take that public key and calculate the private key behind it, potentially allowing an attacker to steal the coins from that address
Newer Bitcoin address formats (like P2PKH and Taproot) hide the public key until use, which helps a bit, but if a quantum computer can crack the signature quickly enough, it could even intercept an outgoing transaction and steal the funds before the transaction confirms on the blockchain.
Ethereum has a similar issue: it uses an account model where the public key is essentially visible for each account (especially once you’ve made a transaction). This means Ethereum accounts are also vulnerable to a quantum attack that can derive private keys.
In short, any cryptocurrency that relies on ECDSA or similar public-key crypto (which is most of them) faces this risk. A quantum attacker could steal crypto holdings by targeting exposed public keys.
Blockchain Infrastructure and Consensus
Beyond individual wallets, the very process that keeps a blockchain running could be at risk. Consider Bitcoin’s Proof-of-Work mining: miners compete to solve a cryptographic puzzle to add the next block. A quantum computer might solve these puzzles much faster than all the other miners, potentially giving a quantum-equipped miner disproportionate control (they could outpace others and perhaps even rewrite blocks).
It’s still debated how realistic this scenario is, because quantum speed-ups for mining might not be straightforward – but it’s a concern. For Proof-of-Stake systems (like Ethereum’s current consensus), the threat is that quantum computers could forge the digital signatures (e.g. BLS signatures) validators use to prove their identity and commitments.
In a worst-case scenario, an attacker with a quantum computer might impersonate validators or forge consensus votes, undermining the integrity of the blockchain’s ledger.

Practical Example: How El Salvador Reduced Quantum Risk
El Salvador split its national BTC reserve across new addresses in 2025 to keep public keys hidden until use, reducing future quantum exposure.
Quantum Risks for Self-Custody Wallet Users
If you use a hot wallet like MetaMask (or Trust Wallet, Exodus, etc.) to manage your cryptocurrency, you are in control of your private keys. “Not your keys, not your coins,” as the saying goes – which is great for sovereignty, but it also means you are responsible for the security of those keys. Under today’s conditions, a well-generated 256-bit private key is essentially unbreakable for any classical computer. Unfortunately, a future CRQC could dramatically change that.
Here’s how a quantum attack could play out for a self-custody wallet user:
Public Exposure of Keys
When a wallet is created, it generates a private key and a corresponding public key. On Ethereum, the address is derived from the public key. On Bitcoin, the key is revealed once funds are spent. This means that after your first transaction, your public key is visible. A CRQC could one day calculate your private key from it, giving attackers full control over your funds.
Hot Wallet Specifics
Hot wallets like MetaMask store keys on internet-connected devices, which are already vulnerable to phishing or malware. Quantum adds another layer. Once your public key is exposed, a CRQC could eventually crack it. On-chain, there is no extra safeguard. If the private key is known, the network accepts any transaction signed with it.
Cold Wallets and “Sleeping” Addresses
Coins held in cold storage, where the public key has never been broadcast, are safer for now since attackers have nothing to calculate against. The moment those funds are moved, the public key is exposed and becomes vulnerable. This is why long-term holders will eventually need to migrate assets into quantum-safe wallets once the technology is available.
Quantum Risks for Exchange Users
Maybe you’re thinking, “Well, I keep my coins on a big exchange like Binance or Coinbase. They handle the keys, so I should be fine, right?” It’s true that when you use a centralized exchange, you are not directly managing the private keys, the exchange is. But that just shifts the target: a quantum attacker would then focus on the exchange’s systems. Here’s how quantum risk plays out for exchange users:
- Exchange Wallets:
Exchanges hold assets in a mix of hot wallets (online) and cold wallets (offline). These are secured with the same cryptography as personal wallets, usually ECDSA. A CRQC could compromise those keys, and because exchanges pool funds, one breach could expose assets belonging to thousands of users.
- Communications and Logins:
Exchanges also rely on TLS (the “https” lock in your browser) to protect logins and API calls. A quantum computer could eventually break these protocols, exposing passwords, 2FA codes, or even altering transactions in transit. This shows the risk isn’t just on-chain, it extends to how users access their accounts.
- Exchange Preparedness:
Top exchanges are already exploring quantum-resistant solutions, building crypto-agility into their systems so they can switch to new algorithms when needed. Others may lag. This is why users should prioritize platforms that go beyond standard 2FA and phishing protections, and that are clearly investing in quantum-safe infrastructure for the future.
NIST and New Algorithms
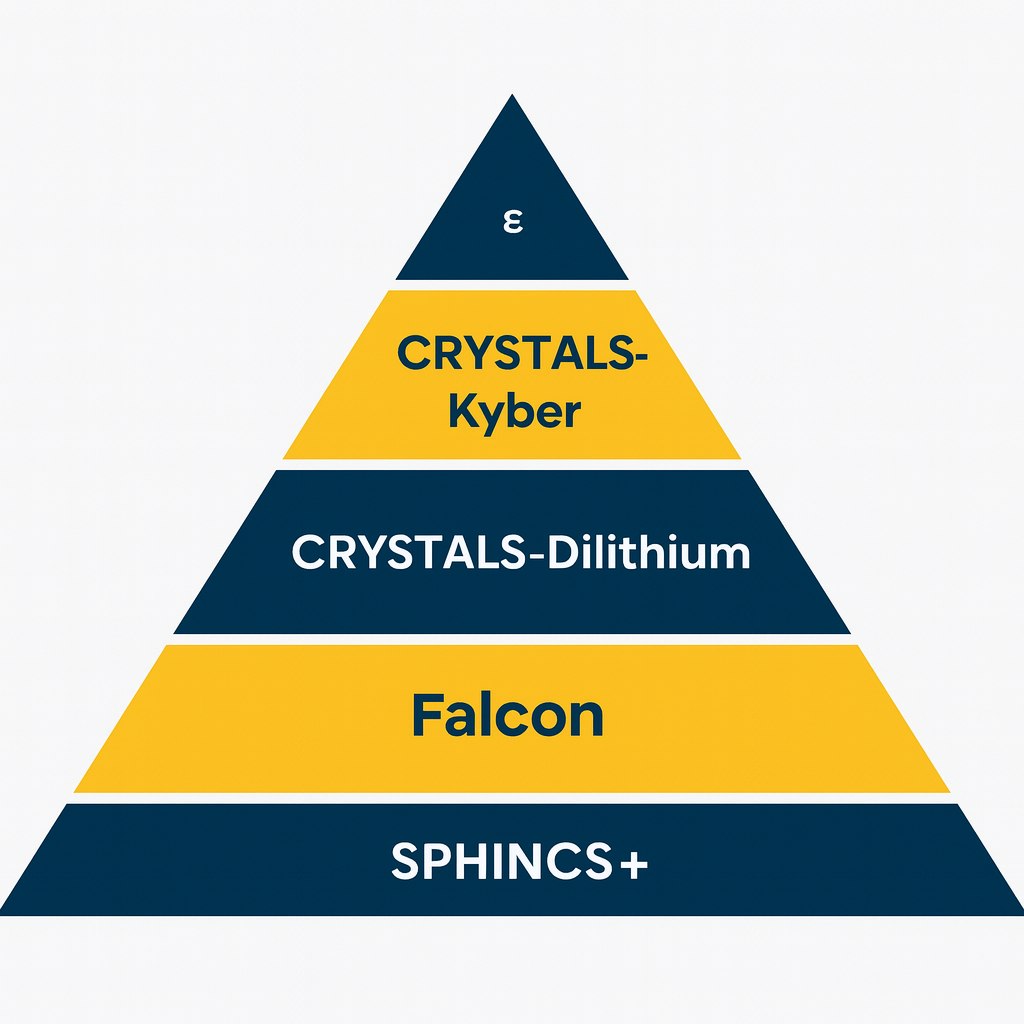
The U.S. National Institute of Standards and Technology (NIST) has been leading a global effort to identify and standardize quantum-resistant algorithms. In 2022, after a multi-year competition, NIST announced a set of finalist algorithms. By August 2024, they finalized the first three post-quantum standards: one for key encapsulation (used in encryption/key exchange) and two for digital signatures.
These include lattice-based algorithms (related to complex structures in math that even quantum finds tough) and hash-based signatures, among others. The names of some of these algorithms are CRYSTALS-Kyber (for key exchange), CRYSTALS-Dilithium (for signatures), Falcon (another signature scheme), and a few others like SPHINCS+ (hash-based signatures).
These algorithms have been vetted by cryptographers worldwide and so far appear to resist known quantum solving methods. For safety, NIST even picked some backup options (like an algorithm called HQC based on error-correcting codes) to diversify the defense in case any one math approach gets compromised.
Also read: SEC Task Force Reviews Quantum-Proof Plan for Digital Assets
Practical Tips for Crypto Users
You don’t need to wait for post-quantum wallets to take precautions. Here are steps you can follow now to reduce risk and stay prepared.
- Keep Software Updated
Always update wallet apps, browser extensions like MetaMask, hardware wallet firmware, and exchange apps. Developers are already building in the foundations for quantum-safe upgrades, and updates ensure you get them.
- Avoid Reusing Addresses
Each time you reuse an address, you expose the same public key. In Bitcoin, use fresh addresses when possible. In Ethereum, where this isn’t built in, consider migrating larger holdings to new wallets periodically. Less exposure means less risk from Harvest Now, Decrypt Later attacks.
- Use Cold Storage for Long-Term Holds
Funds in hardware wallets or paper wallets that haven’t signed transactions are safer for now since their public keys are hidden. While not a permanent solution, cold storage buys time until quantum-safe addresses are available.
- Enable Strong Account Security
Use two-factor authentication (preferably via an authenticator app or hardware key) and strong, unique passwords. These protect against everyday hacks, which remain the more immediate threat compared to quantum.
- Choose Security-Conscious Platforms
Prefer exchanges and custodians that take security seriously and openly discuss future-proofing, including quantum safety. A proactive platform today is more likely to be prepared tomorrow.
Navigating the Quantum Future of Crypto
Quantum computing poses a real threat to the cryptography protecting digital assets, but the industry is preparing. Regulators, developers, and exchanges are working on post-quantum solutions like PQC and hybrid systems, aiming for a smooth migration before CRQCs become practical. For everyday users, the focus is simple: keep software updated, avoid unnecessary key exposure, diversify storage, and follow trusted platforms that take security seriously.
Crypto has faced many challenges and adapted, and quantum will be no different. With vigilance and cooperation, the transition can be managed. The future of digital assets remains strong as long as users and institutions prepare early for a quantum-safe world.
FAQs
1. Can quantum computers break Bitcoin or Ethereum today?
No. Current quantum machines are far too weak to break ECDSA or RSA. The concern is about future CRQCs, which experts believe could arrive in the next decade or two.
2. What is “Harvest Now, Decrypt Later”?
It’s when attackers collect encrypted data or public keys today, planning to crack them once quantum computers are strong enough. This makes early preparation important.
3. Are cold wallets safe from quantum attacks?
Cold wallets are safer because their public keys stay hidden until you spend from them. But once a transaction is made, that address becomes vulnerable, so long-term holders will need to migrate funds to quantum-safe addresses in the future.
4. Will centralized exchanges handle quantum safety for me?
Exchanges are responsible for upgrading their systems, but their readiness will vary. Larger platforms are more likely to adopt hybrid cryptography early. Users should choose security-focused exchanges and stay updated on their quantum transition plans.
5. Does quantum mean the end of crypto?
No. The industry is already developing solutions like PQC, hybrid signatures, and quantum-safe protocols. The transition will be challenging but manageable, much like past upgrades in internet and blockchain security.